Cloud cameras are surveillance cameras connected to the Internet. Costs associated with conventional systems, such as recording servers, construction costs, and operational costs, can be significantly reduced*. The running cost is the monthly fee only.
*Equipment installation and construction costs will be charged separately.
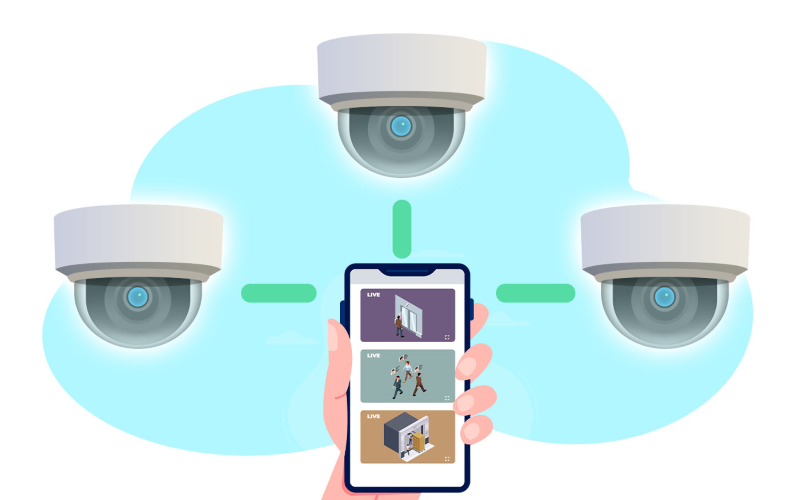
Features of Cloud Camera

Maintenance / Theft Free Servers
Customers do not have to worry about regular replacement or repair of HDDs. The latest version of the software is always available. Since there is no need to place a recorder, it cannot be stolen or destroyed physically.

FHD (2 megapixel) Recording
It supports recording in FHD (2-megapixel) resolution for clear and sharp viewing of even the smallest details. The camera can be used in a wide range of applications.
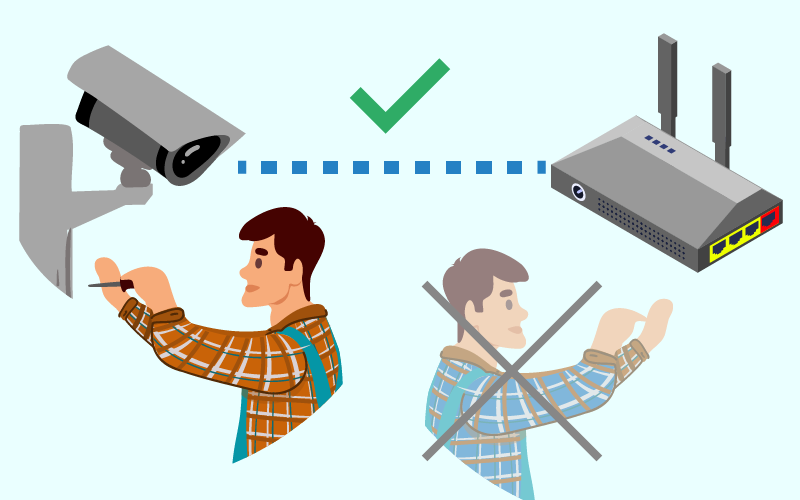
No Configuration Work to Router Required
Since the camera transmits directly to the server, no new configuration is required on the router, even if there is an existing router.

Camera Connection Status Check and Error Notification by Email
It monitors whether customer cameras are connected properly using the LifeCheck server in the cloud. If a connection error occurs with a camera installed in no-man environment, you do not have to worry because it is notified automatically to a designated e-mail address.

Data Saved to SD Card in Network Disconnection
If an SD card is inserted in the camera, recorded data is automatically saved to the SD card in the event of a network disconnection. Stored data is automatically uploaded to the cloud upon network restoration.

Connection Logs Available to Check History
You can grant special login accounts permission to view connection logs. Authorized login accounts can view a user's login/logout history from the connection log view page.

Connection Source Restriction for Unregistered Terminals
By using MAC addresses and IP addresses, the connection source can be restricted for each login account. By limiting login to specific PCs and smartphones, the system prevents connections by unregistered devices and access by unauthorized persons, thereby enhancing operational security. (paid option)






